Google’s New Family Link Software
Wilson Rothman, WSJ personal technology editor explained on Lunch Break with Tanya Rivero that Alphabet Inc’s Google had revealed an unparalleled set of parental controls, with the beta launch of Family Link, while enabling children below the age of 13 to sign for content-restricted accounts.Parents seems to be losing control with their children and tablets, phone as well as iPods have been pushing our kids in a digital black hole enabling less visibility in their social activities and their pastimes. Google’s new Family Link software is a relief for parents in keeping their kids under control in this digital world.
The arrival of Family Link corresponds with a change to the policy of Google on child accounts. Children below 13 years can now have them provided they are set up through the Family Link which has been authorized by a parent.
It is said to be the most inclusive set of parent tools for the internet, the greatest features which Amazon as well as Apple have provided with services of Google which is that we get this remarkable functionality by providing a little more personal information and this time it is data about the online activities of our children.
Experience Use of Android Based Device
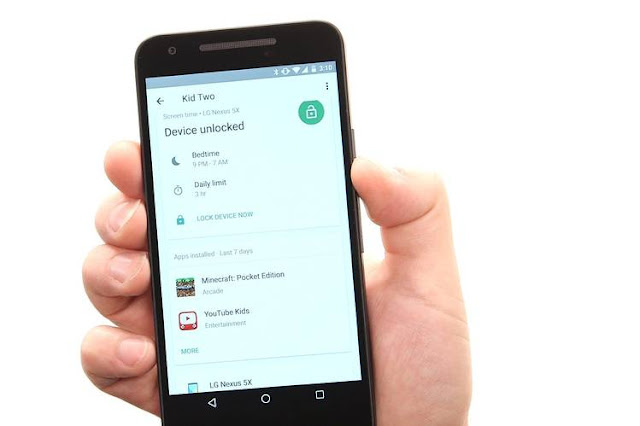
With the Family Link account a child is capable of experiencing the use of an Android based device and the test case, a Nexus 5X in a manner which tends to look adequately like the phone of Mom or Dad’s though tends to keep the child protected from some trouble of adulthood in Google search, Chrome browser, Google Play store together with YouTube app.Harmless search that seems to yield filtered, child-sanitized web as well as image search consequences could be through default. Google has also mentioned that search effects could, for the first time, cater to children but that would be difficult to tell. The amazing thing is for parents in the form of remote access.
Moreover, Family Link also tends to provide parents with an administrative app which they could utilise in locating the device of their child onmany ring it in case of losing in couch cushions, remotely adjust account and device settings or also do a factory-reset if the phone is lost.
Set Up Time Restrictions/Off-limits Hours
Moreover parents could also set up time restrictions and off-limits hours and see the time spent on several app by their children. As the beta version of the Family Link tends to go public individuals could request to try it though their devices need to be running Nougat which is the updated version of Android.Google has informed that by the end of the year, it would be working with earlier versions. The company also believes in releasing a parental control app for iPhones. It is essential to know how many parental control systems are available before one decides to purchase it. They are not just built into popular devices led by Apple and Amazon but are also sold as services by third party.
Apple is said to have control both local and remote dispersed around the operating system of its iOS. The restriction unit in the setting of iOS enables the user to set a passcode in locking down from Siri and FaceTime to iTunes albums together with the feared in-app procurements