It was just last month that is in September one of the largest net attacks took place with pinpointed a renowned OVH a French hosting firm and a blogger. This single attack is believed to have comprised of over one trillion bits of data. Both of the hacking events marked a change in the methods used by hackers who survive by breaking into websites which hold widespread data add this form of attacks is known as Distributed Denial of Service attacks (DDoS). The data was sent to the targets through and other such "smart" devices which were hijacked by the hackers.
Can I tell if my webcam/DVR/printer is attacking someone?
Well to be honest, not easily. If you are a medium of bombarding someone else, your internet speed may slow down however it may not be noticed at times of normal browsing while it may be evident when it comes to video or music streaming or games which will lag. For those who are tech savvy, they can make use of software’s which keep a tab on the flow of data packs on their home network, however this is not easy if you are unaware of what you are doing exactly.
Could I get in trouble for letting my webcam attack someone?
In terms of legality, you can’t get into trouble with the police however it is believed through researches that a hacker can get into your internal network through a webcam hack and keep a tab on everything else. So in such a case you have an intruder which is best if gotten rid of by taking the necessary action.
Why are malicious hackers using these devices?
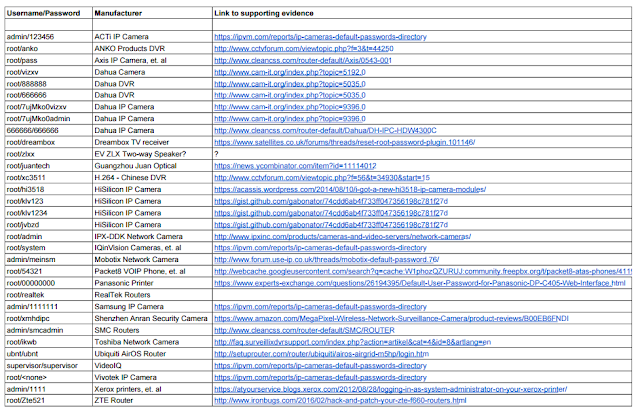
That’s because it is way easier to hack in comparison to PCs or servers and these devices tend to make use of default passwords and fail to have any kind of security software in place. And to the benefit of the hackers, there are endless numbers that stay on all day long and it is a task to both update as well as secure. In modern days it is extremely easy for hackers, they are able to target vulnerable devices and put together an army of their own to create a botnet without having to rent hijacked machines like in the past.
What kind of devices are they scanning for?
Web-associated cameras are especially prominent however outputs are likewise being completed for advanced TV recorders, home routers and printers. All these have a fundamental processor inside that can be subverted to pump out attack packets. Brian Krebs, the blogger who experienced an assault an IoT botnet, has ordered a rundown of gadgets known to have misused his webpage with information. Large portions of the login names and passwords for these gadgets are anything but difficult to-crack. On 1 October, source code for one IoT assault was freely shared, driving some to propose that numerous more malignant programmers will now begin checking for vulnerable gadgets. This guide made by security firm Symantec demonstrates where Europe's botnets are facilitated. Turkey is home to the vast majority of the commandeered devices and PCs.
How new are these types of attacks?
The main DDoS assaults were seen on the web in 2000. The primary influx of information bombardments was gone for betting locales which were undermined with being thumped disconnected unless they paid an expense. The greater part of those coercion endeavors utilized commandeered PCs to send information. Presently the ascent of the Internet of Things that is populated with brilliant gadgets has commenced recharged enthusiasm for these sorts of assaults. Security scientists have cautioned about the perils of unreliable IoT gadgets for quite a while yet they are beginning to be utilized for critical assaults sooner than numerous individuals anticipated.