Perovskites – Cheap/Easy/Flexible
Perovskites has taken the solar cell industry by storm in recent years. They tend to be cheap, easy in producing as well as flexible in their applications.Moreover their efficiency in converting light into electricity has developed quicker than that of any other material from under 4% in 2009 to over 20% in 2017, where some of the experts are of the belief that Perovskites Solar Cells could ultimately outperform the most common solar cell material, silicon. However, irrespective of their reputation, researchers are not aware why perovskites solar cells tend to be so efficient.
Research had been carried out with powerful `electron camera’ at the Department of energy’s SLAC National Accelerator Laboratory which has now revealed that light whirls atoms around in perovskites, potentially explaining the high efficiency of these next –generation solar cell materials as well as provides clues in making improved ones.
Aaron Lindenberg from Stanford Institute for Materials and Energy Sciences – SIMES and the Stanford PULSE Institute for ultrafast science that had jointly operated by Stanford University and SLAC, had stated that they have taken a step towards resolving the mystery.
He further added that they had recorded movies which tend to show that certain atoms in a perovskite seem to respond to light within trillionths of a second in a very unusual manner.
Flexibility Based on Atomic Structure of Material
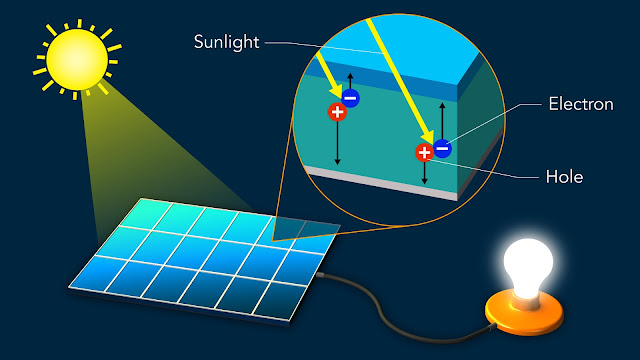
This could facilitate the transport of electric charges through the material and enhance its efficiency. The study had been published recently in Science Advances. When light is said to shine on perovskites solar cell material, its energy tends to displace some of the negative charged electrons of the material.
This is inclined to leave behind `electron holes’ having positive charge where the electrons had initially been located. Electrons and holes tend to migrate in opposite sides of the material thereby developing a voltage which could be utilised to power electrical devices. The efficiency of perovskites solar cell seems to depend on how freely electrons as well as holes tend to move in the material.
In turn, their flexibility is based on the atomic structure of the material. In silicon solar cells for instance, silicon atoms is said to line up in an orderly manner within crystals as well as the smallest structural defects tend to reduce the ability of the material to harvest light efficiently.
As a consequence, silicon crystals need to be grown in costly multistep process under very clean conditions while perovskites are said to be produced with the combination of chemicals in a solvent that tends to evaporate to leave an extremely thin film of perovskite material according to the study’s lead author from SIMES at SLAC, Xiaoxi Wu.
Lower Cost/Lightweight
He further added that simpler processing would mean lower costs and unlike silicon solar cells, perovskite thin films seems to be lightweight as well as flexible and can be applied with ease to virtually any surface. With regards to perovskites what is it that permits some of them to harvest light in an efficient manner?
Scientists are of the opinion that one of the keys is how their atoms tend to move in reaction to light. In order to get a better understanding, Wu together with his colleagues researched on these motions in a prototype material made of iodine, lead together with an organic molecule known as methylammonium.
The iodine atoms tend to be arranged in octohedra, eight-sided structures which seems like two pyramids that is joined towards the base. The lead atom tends to sit inside the octohedra and the methylammonium molecule is between octohedra.
The architecture seems common to several of the perovskites investigated for perovskites solar cell applications. The earlier research could have explored mostly the role of the mehylammonium ions together with their motions in transporting electric charge through the material.
Light Cause of Huge Deformation in Network
Wu had stated that they had found that light is the cause of huge deformations in the network of lead and iodine atoms which tend to be crucial for the efficiency of perovskites. At the Accelerator Structure Test Area – ASTA of SLAC, the researchers had initially hit a perovskite film which was less than two millionths of an inch thick having a 40-femtosecond laser pulse.
One femtosecond is said to be a millionth of a billionth of a second and in order to determine the atomic response, they directed a 300-femtosecond pulse of highly energetic electrons via the material and noticed how the electrons had been deflected in the film. This system known as ultrafast electron diffraction – UED enabled them to reconstruct the atomic structure. The speedy improvement of perovskite solar cells has enhanced them in the photovoltaics world as well as of high interest to the academic community.
While the operational system seems to be comparatively new, there are possibilities of additional research in the basic physics and chemistry regarding perovksites. Moreover, from observations of past two years, the engineering development of perovskite formulation together with the fabrication sequences has given rise to significant increases in power conversion efficiency.